Particular because of Vlad Zamfir, Chris Barnett and Dominic Williams for concepts and inspiration
In a recent blog post I outlined some partial options to scalability, all of which match into the umbrella of Ethereum 1.0 because it stands. Specialised micropayment protocols resembling channels and probabilistic fee techniques might be used to make small funds, utilizing the blockchain both just for eventual settlement, or solely probabilistically. For some computation-heavy functions, computation may be completed by one social gathering by default, however in a method that may be “pulled down” to be audited by your complete chain if somebody suspects malfeasance. Nevertheless, these approaches are all essentially application-specific, and much from supreme. On this publish, I describe a extra complete method, which, whereas coming at the price of some “fragility” considerations, does present an answer which is far nearer to being common.
Understanding the Goal
To begin with, earlier than we get into the small print, we have to get a a lot deeper understanding of what we truly need. What can we imply by scalability, significantly in an Ethereum context? Within the context of a Bitcoin-like forex, the reply is comparatively easy; we would like to have the ability to:
- Course of tens of 1000’s of transactions per second
- Present a transaction charge of lower than $0.001
- Do all of it whereas sustaining safety towards a minimum of 25% assaults and with out extremely centralized full nodes
The primary purpose alone is straightforward; we simply take away the block dimension restrict and let the blockchain naturally develop till it turns into that enormous, and the financial system takes care of itself to drive smaller full nodes to proceed to drop out till the one three full nodes left are run by GHash.io, Coinbase and Circle. At that time, some stability will emerge between charges and dimension, as excessize dimension results in extra centralization which ends up in extra charges as a consequence of monopoly pricing. With the intention to obtain the second, we will merely have many altcoins. To realize all three mixed, nonetheless, we have to break by way of a elementary barrier posed by Bitcoin and all different current cryptocurrencies, and create a system that works with out the existence of any “full nodes” that have to course of each transaction.
In an Ethereum context, the definition of scalability will get a little bit extra difficult. Ethereum is, essentially, a platform for “dapps”, and inside that mandate there are two sorts of scalability which can be related:
- Permit heaps and many folks to construct dapps, and maintain the transaction charges low
- Permit every particular person dapp to be scalable in keeping with a definition much like that for Bitcoin
The primary is inherently simpler than the second. The one property that the “construct heaps and many alt-Etherea” method doesn’t have is that every particular person alt-Ethereum has comparatively weak safety; at a dimension of 1000 alt-Etherea, each could be susceptible to a 0.1% assault from the viewpoint of the entire system (that 0.1% is for externally-sourced assaults; internally-sourced assaults, the equal of GHash.io and Discus Fish colluding, would take solely 0.05%). If we will discover a way for all alt-Etherea to share consensus energy, eg. some model of merged mining that makes every chain obtain the energy of your complete pack with out requiring the existence of miners that find out about all chains concurrently, then we might be completed.
The second is extra problematic, as a result of it results in the identical fragility property that arises from scaling Bitcoin the forex: if each node sees solely a small a part of the state, and arbitrary quantities of BTC can legitimately seem in any a part of the state originating from any a part of the state (such fungibility is a part of the definition of a forex), then one can intuitively see how forgery assaults would possibly unfold by way of the blockchain undetected till it’s too late to revert every thing with out substantial system-wide disruption by way of a worldwide revert.
Reinventing the Wheel
We’ll begin off by describing a comparatively easy mannequin that does present each sorts of scalability, however supplies the second solely in a really weak and dear method; basically, we’ve got simply sufficient intra-dapp scalability to make sure asset fungibility, however not way more. The mannequin works as follows:
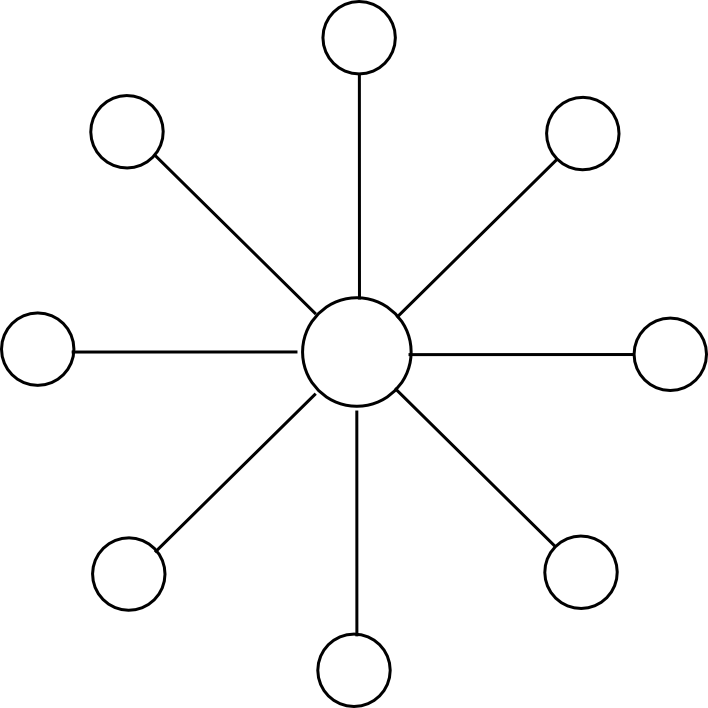
Suppose that the worldwide Ethereum state (ie. all accounts, contracts and balances) is cut up up into N elements (“substates”) (assume 10 <= N <= 200). Anybody can arrange an account on any substate, and one can ship a transaction to any substate by including a substate quantity flag to it, however unusual transactions can solely ship a message to an account in the identical substate because the sender. Nevertheless, to make sure safety and cross-transmissibility, we add some extra options. First, there’s additionally a particular “hub substate”, which comprises solely an inventory of messages, of the shape [dest_substate, address, value, data]. Second, there’s an opcode CROSS_SEND, which takes these 4 parameters as arguments, and sends such a one-way message enroute to the vacation spot substate.
Miners mine blocks on some substate s[j], and every block on s[j] is concurrently a block within the hub chain. Every block on s[j] has as dependencies the earlier block on s[j] and the earlier block on the hub chain. For instance, with N = 2, the chain would look one thing like this:
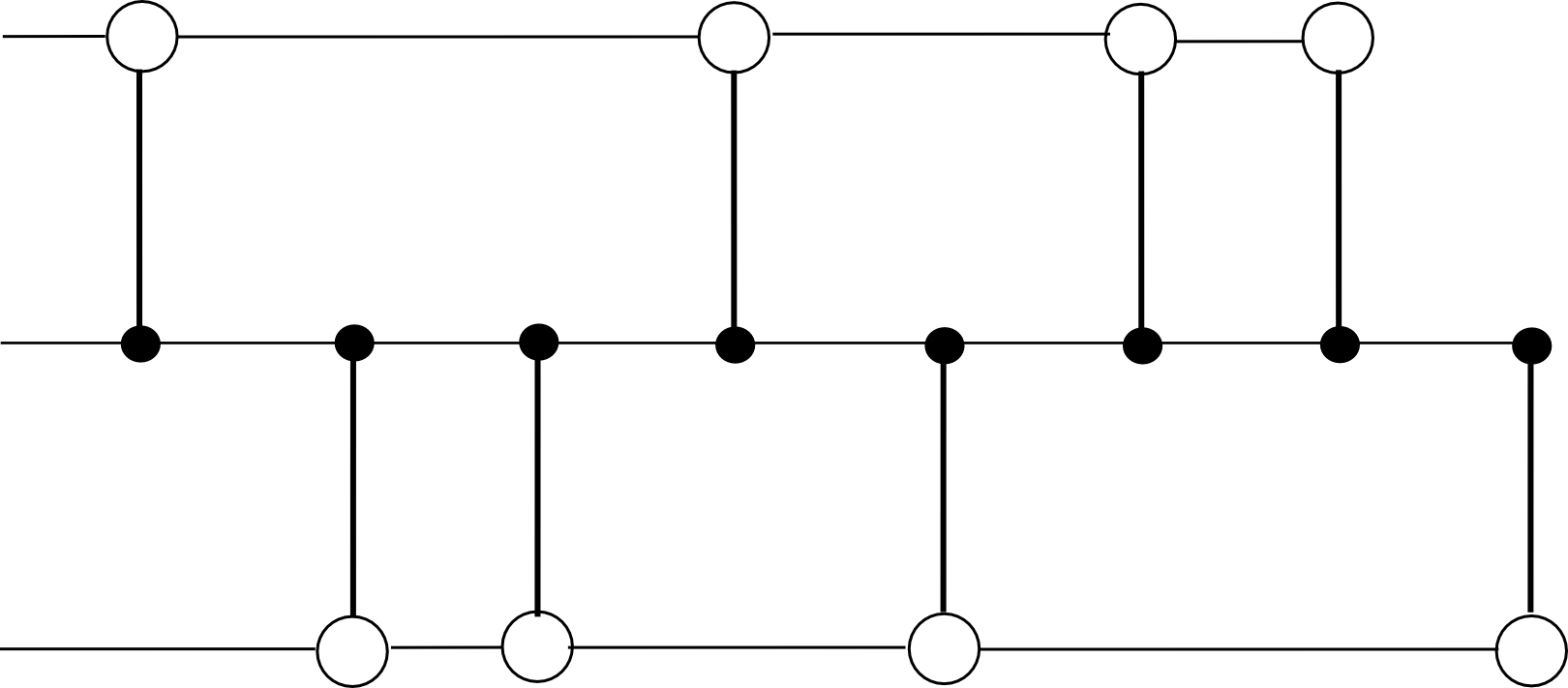
The block-level state transition operate, if mining on substate s[j], does three issues:
- Processes state transitions within s[j]
- If any of these state transitions creates a CROSS_SEND, provides that message to the hub chain
- If any messages are on the hub chain with dest_substate = j, removes the messages from the hub chain, sends the messages to their vacation spot addresses on s[j], and processes all ensuing state transitions
From a scalability perspective, this provides us a considerable enchancment. All miners solely want to concentrate on two out of the whole N + 1 substates: their very own substate, and the hub substate. Dapps which can be small and self-contained will exist on one substate, and dapps that wish to exist throughout a number of substates might want to ship messages by way of the hub. For instance a cross-substate forex dapp would preserve a contract on all substates, and every contract would have an API that permits a person to destroy forex models inside of 1 substate in change for the contract sending a message that may result in the person being credited the identical quantity on one other substate.
Messages going by way of the hub do have to be seen by each node, so these might be costly; nonetheless, within the case of ether or sub-currencies we solely want the switch mechanism for use often for settlement, doing off-chain inter-substate change for many transfers.
Assaults, Challenges and Responses
Now, allow us to take this easy scheme and analyze its safety properties (for illustrative functions, we’ll use N = 100). To begin with, the scheme is safe towards double-spend assaults as much as 50% of the whole hashpower; the reason being that each sub-chain is basically merge-mined with each different sub-chain, with every block reinforcing the safety of all sub-chains concurrently.
Nevertheless, there are extra harmful courses of assaults as nicely. Suppose {that a} hostile attacker with 4% hashpower jumps onto one of many substates, thereby now comprising 80% of the mining energy on it. Now, that attacker mines blocks which can be invalid – for instance, the attacker features a state transition that creates messages sending 1000000 ETH to each different substate out of nowhere. Different miners on the identical substate will acknowledge the hostile miner’s blocks as invalid, however that is irrelevant; they’re solely a really small a part of the whole community, and solely 20% of that substate. The miners on different substates do not know that the attacker’s blocks are invalid, as a result of they don’t have any data of the state of the “captured substate”, so at first look it appears as if they could blindly settle for them.
Thankfully, right here the answer right here is extra advanced, however nonetheless nicely inside the attain of what we presently know works: as quickly as one of many few respectable miners on the captured substate processes the invalid block, they may see that it is invalid, and due to this fact that it is invalid in some explicit place. From there, they may have the ability to create a light-client Merkle tree proof displaying that that exact a part of the state transition was invalid. To clarify how this works in some element, a lightweight consumer proof consists of three issues:
- The intermediate state root that the state transition began from
- The intermediate state root that the state transition ended at
- The subset of Patricia tree nodes which can be accessed or modified within the technique of executing the state transition
The primary two “intermediate state roots” are the roots of the Ethereum Patricia state tree earlier than and after executing the transaction; the Ethereum protocol requires each of those to be in each block. The Patricia state tree nodes supplied are wanted so as to the verifier to observe alongside the computation themselves, and see that the identical result’s arrived on the finish. For instance, if a transaction finally ends up modifying the state of three accounts, the set of tree nodes that may have to be supplied would possibly look one thing like this:
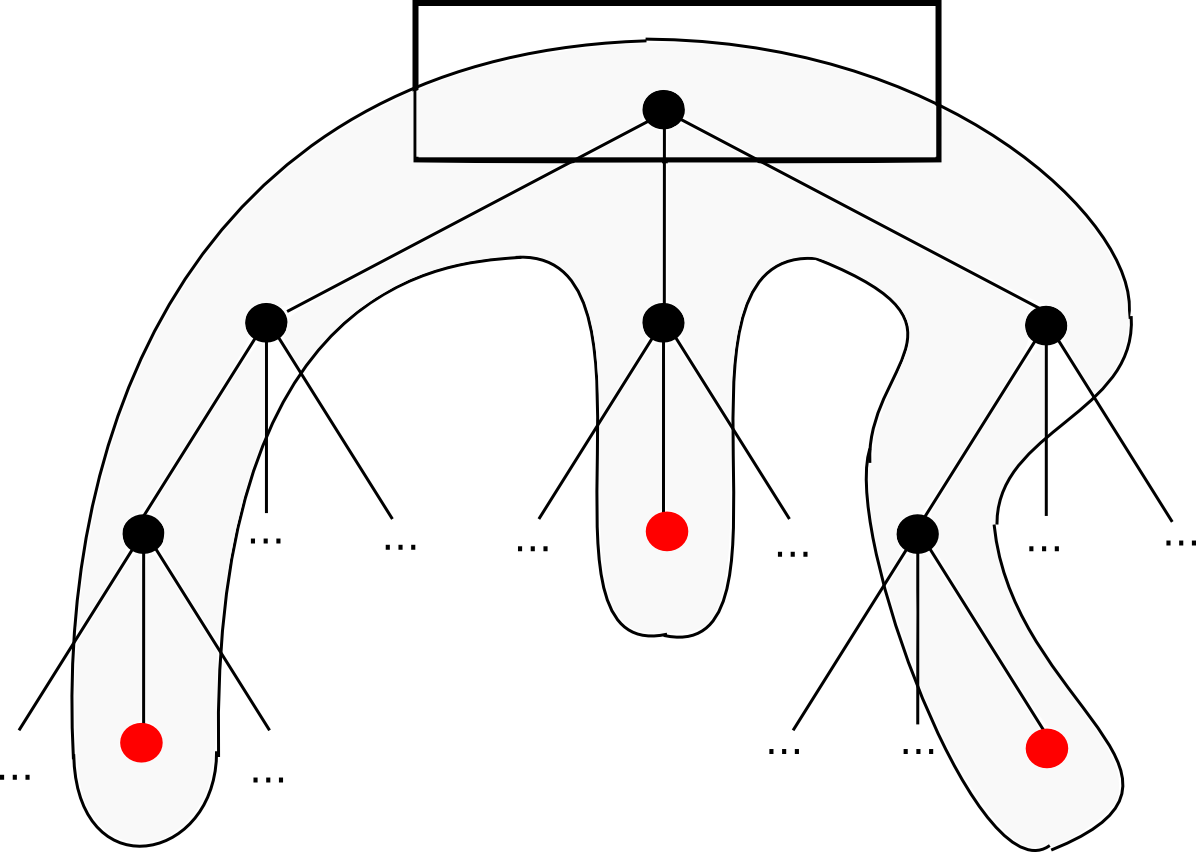
Technically, the proof ought to embody the set of Patricia tree nodes which can be wanted to entry the intermediate state roots and the transaction as nicely, however that is a comparatively minor element. Altogether, one can consider the proof as consisting of the minimal quantity of knowledge from the blockchain wanted to course of that exact transaction, plus some additional nodes to show that these bits of the blockchain are literally within the present state. As soon as the whistleblower creates this proof, they may then be broadcasted to the community, and all different miners will see the proof and discard the faulty block.
The toughest class of assault of all, nonetheless, is what known as a “knowledge unavailability assault”. Right here, think about that the miner sends out solely the block header to the community, in addition to the listing of messages so as to add to the hub, however doesn’t present any of the transactions, intermediate state roots or the rest. Now, we’ve got an issue. Theoretically, it’s completely attainable that the block is totally respectable; the block may have been correctly constructed by gathering some transactions from just a few millionaires who occurred to be actually beneficiant. In actuality, in fact, this isn’t the case, and the block is a fraud, however the truth that the information just isn’t obtainable in any respect makes it not possible to assemble an affirmative proof of the fraud. The 20% trustworthy miners on the captured substate could yell and squeal, however they don’t have any proof in any respect, and any protocol that did heed their phrases would essentially fall to a 0.2% denial-of-service assault the place the miner captures 20% of a substate and pretends that the opposite 80% of miners on that substate are conspiring towards him.
To unravel this drawback, we want one thing known as a challenge-response protocol. Basically, the mechanism works as follows:
- Sincere miners on the captured substate see the header-only block.
- An trustworthy miner sends out a “problem” within the type of an index (ie. a quantity).
- If the producer of the block can submit a “response” to the problem, consisting of a light-client proof that the transaction execution on the given index was executed legitimately (or a proof that the given index is bigger than the variety of transactions within the block), then the problem is deemed answered.
- If a problem goes unanswered for just a few seconds, miners on different substates contemplate the block suspicious and refuse to mine on it (the game-theoretic justification for why is similar as at all times: as a result of they think that others will use the identical technique, and there’s no level mining on a substate that may quickly be orphaned)
Word that the mechanism requires just a few added complexities on order to work. If a block is revealed alongside all of its transactions apart from just a few, then the challenge-response protocol may rapidly undergo all of them and discard the block. Nevertheless, if a block was revealed really headers-only, then if the block contained a whole bunch of transactions, a whole bunch of challenges could be required. One heuristic method to fixing the issue is that miners receiving a block ought to privately choose some random nonces, ship out just a few challenges for these nonces to some identified miners on the possibly captured substate, and if responses to all challenges don’t come again instantly deal with the block as suspect. Word that the miner does NOT broadcast the problem publicly – that may give a chance for an attacker to rapidly fill within the lacking knowledge.
The second drawback is that the protocol is susceptible to a denial-of-service assault consisting of attackers publishing very very many challenges to respectable blocks. To unravel this, making a problem ought to have some price – nonetheless, if this price is just too excessive then the act of constructing a problem would require a really excessive “altruism delta”, maybe so excessive that an assault will ultimately come and nobody will problem it. Though some could also be inclined to resolve this with a market-based method that locations accountability for making the problem on no matter events find yourself robbed by the invalid state transition, it’s value noting that it is attainable to provide you with a state transition that generates new funds out of nowhere, stealing from everybody very barely by way of inflation, and likewise compensates rich coin holders, making a theft the place there is no such thing as a concentrated incentive to problem it.
For a forex, one “simple answer” is capping the worth of a transaction, making your complete drawback have solely very restricted consequence. For a Turing-complete protocol the answer is extra advanced; the perfect approaches probably contain each making challenges costly and including a mining reward to them. There might be a specialised group of “problem miners”, and the speculation is that they are going to be detached as to which challenges to make, so even the tiniest altruism delta, enforced by software program defaults, will drive them to make appropriate challenges. One could even attempt to measure how lengthy challenges take to get responded, and extra extremely reward those that take longer.
The Twelve-Dimensional Hypercube
Word: that is NOT the identical because the erasure-coding Borg dice. For more information on that, see right here: https://blog.ethereum.org/2014/08/16/secret-sharing-erasure-coding-guide-aspiring-dropbox-decentralizer/
We will see two flaws within the above scheme. First, the justification that the challenge-response protocol will work is fairly iffy at finest, and has poor degenerate-case conduct: a substate takeover assault mixed with a denial of service assault stopping challenges may probably drive an invalid block into a series, requiring an eventual day-long revert of your complete chain when (if?) the smoke clears. There’s additionally a fragility part right here: an invalid block in any substate will invalidate all subsequent blocks in all substates. Second, cross-substate messages should nonetheless be seen by all nodes. We begin off by fixing the second drawback, then proceed to point out a attainable protection to make the primary drawback barely much less unhealthy, after which lastly get round to fixing it fully, and on the similar time eliminating proof of labor.
The second flaw, the expensiveness of cross-substate messages, we remedy by changing the blockchain mannequin from this:

To this:
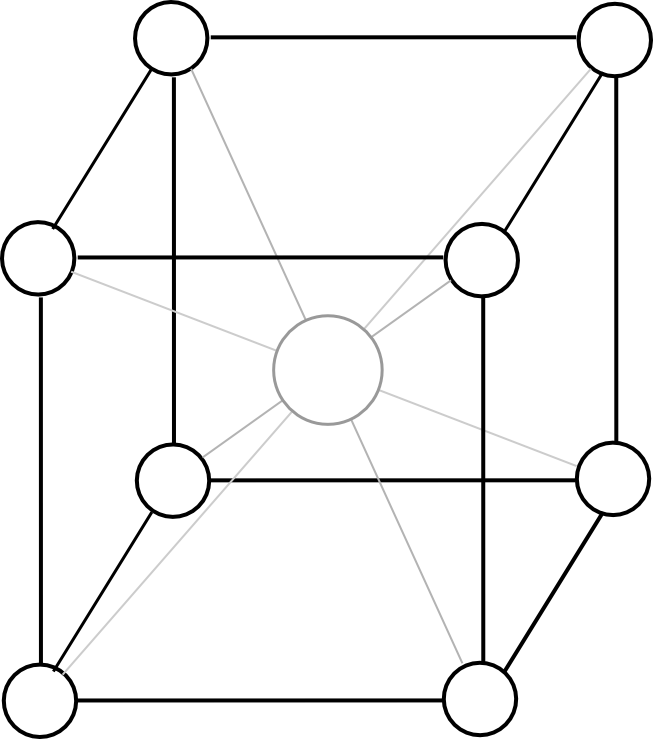
Besides the dice ought to have twelve dimensions as an alternative of three. Now, the protocol appears as follows:
- There exist 2N substates, every of which is recognized by a binary string of size N (eg. 0010111111101). We outline the Hamming distance H(S1, S2) because the variety of digits which can be totally different between the IDs of substates S1 and S2 (eg. HD(00110, 00111) = 1, HD(00110, 10010) = 2, and so forth).
- The state of every substate shops the unusual state tree as earlier than, but additionally an outbox.
- There exists an opcode, CROSS_SEND, which takes 4 arguments [dest_substate, to_address, value, data], and registers a message with these arguments within the outbox of S_from the place S_from is the substate from which the opcode was known as
- All miners should “mine an edge”; that’s, legitimate blocks are blocks which modify two adjoining substates S_a and S_b, and may embody transactions for both substate. The block-level state transition operate is as follows:
- Course of all transactions so as, making use of the state transitions to S_a or S_b as wanted.
- Course of all messages within the outboxes of S_a and S_b so as. If the message is within the outbox of S_a and has last vacation spot S_b, course of the state transitions, and likewise for messages from S_b to S_a. In any other case, if a message is in S_a and HD(S_b, msg.dest) < HD(S_a, msg.dest), transfer the message from the outbox of S_a to the outbox of S_b, and likewise vice versa.
- There exists a header chain protecting observe of all headers, permitting all of those blocks to be merge-mined, and protecting one centralized location the place the roots of every state are saved.
Basically, as an alternative of travelling by way of the hub, messages make their method across the substates alongside edges, and the always decreasing Hamming distance ensures that every message at all times ultimately will get to its vacation spot.
The important thing design determination right here is the association of all substates right into a hypercube. Why was the dice chosen? The easiest way to consider the dice is as a compromise between two excessive choices: on the one hand the circle, and then again the simplex (mainly, 2N-dimensional model of a tetrahedron). In a circle, a message would want to journey on common 1 / 4 of the way in which throughout the circle earlier than it will get to its vacation spot, that means that we make no effectivity beneficial properties over the plain previous hub-and-spoke mannequin.
In a simplex, each pair of substates has an edge, so a cross-substate message would get throughout as quickly as a block between these two substates is produced. Nevertheless, with miners selecting random edges it could take a very long time for a block on the precise edge to look, and extra importantly customers watching a specific substate would have to be a minimum of gentle purchasers on each different substate so as to validate blocks which can be related to them. The hypercube is an ideal stability – every substate has a logarithmically rising variety of neighbors, the size of the longest path grows logarithmically, and block time of any explicit edge grows logarithmically.
Word that this algorithm has basically the identical flaws because the hub-and-spoke method – particularly, that it has unhealthy degenerate-case conduct and the economics of challenge-response protocols are very unclear. So as to add stability, one method is to switch the header chain considerably.
Proper now, the header chain could be very strict in its validity necessities – if any block anyplace down the header chain seems to be invalid, all blocks in all substates on high of which can be invalid and should be redone. To mitigate this, we will require the header chain to easily maintain observe of headers, so it will possibly comprise each invalid headers and even a number of forks of the identical substate chain. So as to add a merge-mining protocol, we implement exponential subjective scoring however utilizing the header chain as an absolute frequent timekeeper. We use a low base (eg. 0.75 as an alternative of 0.99) and have a most penalty issue of 1 / 2N to take away the profit from forking the header chain; for these not nicely versed within the mechanics of ESS, this mainly means “enable the header chain to comprise all headers, however use the ordering of the header chain to penalize blocks that come later with out making this penalty too strict”. Then, we add a delay on cross-substate messages, so a message in an outbox solely turns into “eligible” if the originating block is a minimum of just a few dozen blocks deep.
Proof of Stake
Now, allow us to work on porting the protocol to nearly-pure proof of stake. We’ll ignore nothing-at-stake points for now; Slasher-like protocols plus exponential subjective scoring can remedy these considerations, and we’ll talk about including them in later. Initially, our goal is to point out how you can make the hypercube work with out mining, and on the similar time partially remedy the fragility drawback. We’ll begin off with a proof of activity implementation for multichain. The protocol works as follows:
- There exist 2N substates indentified by binary string, as earlier than, in addition to a header chain (which additionally retains observe of the most recent state root of every substate).
- Anybody can mine an edge, as earlier than, however with a decrease problem. Nevertheless, when a block is mined, it should be revealed alongside the whole set of Merkle tree proofs so {that a} node with no prior info can totally validate all state transitions within the block.
- There exists a bonding protocol the place an handle can specify itself as a possible signer by submitting a bond of dimension B (richer addresses might want to create a number of sub-accounts). Potential signers are saved in a specialised contract C[s] on every substate s.
- Based mostly on the block hash, a random 200 substates s[i] are chosen, and a search index 0 <= ind[i] < 2^160 is chosen for every substate. Outline signer[i] because the proprietor of the primary handle in C[s[i]] after index ind[i]. For the block to be legitimate, it should be signed by a minimum of 133 of the set signer[0] … signer[199].
To really examine the validity of a block, the consensus group members would do two issues. First, they’d examine that the preliminary state roots supplied within the block match the corresponding state roots within the header chain. Second, they’d course of the transactions, and make it possible for the ultimate state roots match the ultimate state roots supplied within the header chain and that every one trie nodes wanted to calculate the replace can be found someplace within the community. If each checks cross, they signal the block, and if the block is signed by sufficiently many consensus group members it will get added to the header chain, and the state roots for the 2 affected blocks within the header chain are up to date.
And that is all there’s to it. The important thing property right here is that each block has a randomly chosen consensus group, and that group is chosen from the worldwide state of all account holders. Therefore, except an attacker has a minimum of 33% of the stake in your complete system, it is going to be just about not possible (particularly, 2-70 chance, which with 230 proof of labor falls nicely into the realm of cryptographic impossiblity) for the attacker to get a block signed. And with out 33% of the stake, an attacker will be unable to stop respectable miners from creating blocks and getting them signed.
This method has the profit that it has good degenerate-case conduct; if a denial-of-service assault occurs, then chances are high that nearly no blocks might be produced, or a minimum of blocks might be produced very slowly, however no injury might be completed.
Now, the problem is, how can we additional cut back proof of labor dependence, and add in blockmaker and Slasher-based protocols? A easy method is to have a separate blockmaker protocol for each edge, simply as within the single-chain method. To incentivize blockmakers to behave truthfully and never double-sign, Slasher will also be used right here: if a signer indicators a block that finally ends up not being in the principle chain, they get punished. Schelling level results make sure that everybody has the motivation to observe the protocol, as they guess that everybody else will (with the extra minor pseudo-incentive of software defaults to make the equilibrium stronger).
A full EVM
These protocols enable us to ship one-way messages from one substate to a different. Nevertheless, a technique messages are restricted in performance (or fairly, they’ve as a lot performance as we would like them to have as a result of every thing is Turing-complete, however they aren’t at all times the nicest to work with). What if we will make the hypercube simulate a full cross-substate EVM, so you’ll be able to even name features which can be on different substates?
Because it seems, you’ll be able to. The secret’s so as to add to messages a knowledge construction known as a continuation. For instance, suppose that we’re in the midst of a computation the place a contract calls a contract which creates a contract, and we’re presently executing the code that’s creating the interior contract. Thus, the place we’re within the computation appears one thing like this:
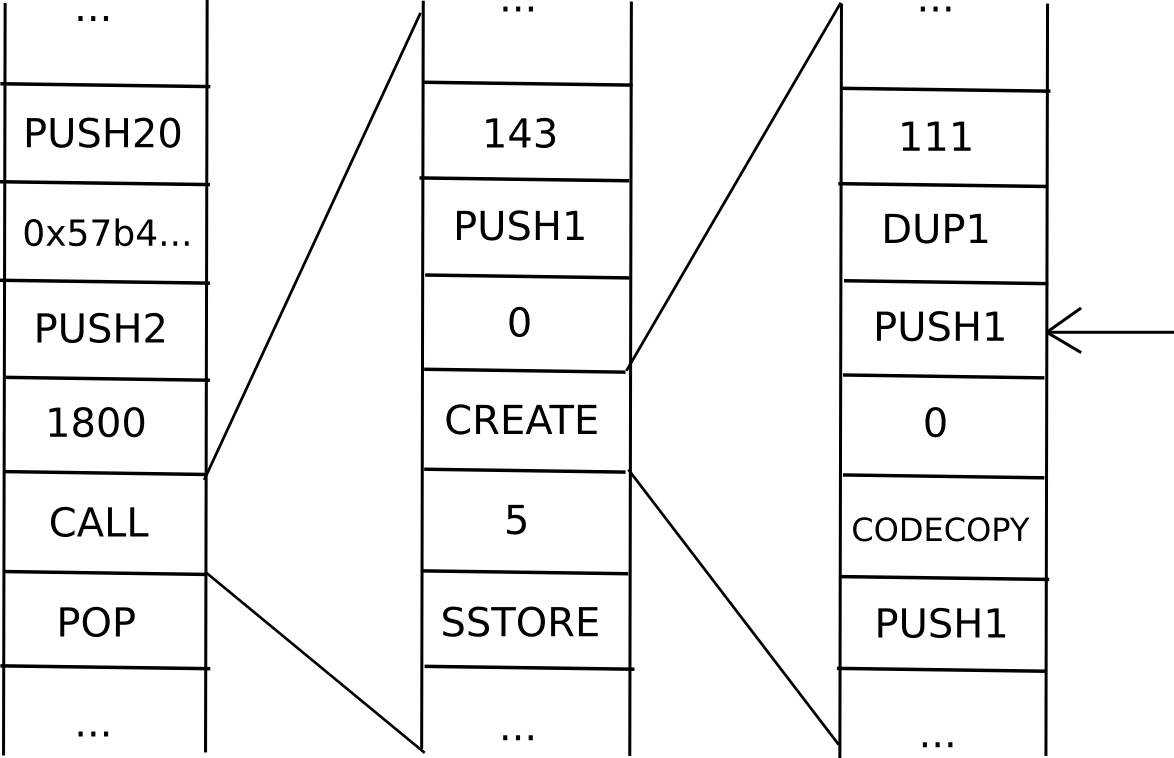
Now, what’s the present “state” of this computation? That’s, what’s the set of all the information that we want to have the ability to pause the computation, after which utilizing the information resume it afterward? In a single occasion of the EVM, that is simply this system counter (ie. the place we’re within the code), the reminiscence and the stack. In a state of affairs with contracts calling one another, we want that knowledge for your complete “computational tree”, together with the place we’re within the present scope, the mum or dad scope, the mum or dad of that, and so forth again to the unique transaction:
That is known as a “continuation”. To renew an execution from this continuation, we merely resume every computation and run it to completion in reverse order (ie. end the innermost first, then put its output into the suitable house in its mum or dad, then end the mum or dad, and so forth). Now, to make a completely scalable EVM, we merely change the idea of a one-way message with a continuation, and there we go.
In fact, the query is, can we even wish to go this far? To begin with, going between substates, such a digital machine could be extremely inefficient; if a transaction execution must entry a complete of ten contracts, and every contract is in some random substate, then the method of operating by way of that complete execution will take a median of six blocks per transmission, occasions two transmissions per sub-call, occasions ten sub-calls – a complete of 120 blocks. Moreover, we lose synchronicity; if A calls B as soon as after which once more, however between the 2 calls C calls B, then C could have discovered B in {a partially} processed state, probably opening up safety holes. Lastly, it is tough to mix this mechanism with the idea of reverting transaction execution if transactions run out of fuel. Thus, it could be simpler to not hassle with continuations, and fairly choose for easy one-way messages; as a result of the language is Turing-complete continuations can at all times be constructed on high.
On account of the inefficiency and instability of cross-chain messages regardless of how they’re completed, most dapps will wish to dwell completely within a single sub-state, and dapps or contracts that incessantly discuss to one another will wish to dwell in the identical sub-state as nicely. To forestall completely everybody from residing on the identical sub-state, we will have the fuel limits for every substate “spill over” into one another and attempt to stay related throughout substates; then, market forces will naturally make sure that widespread substates develop into dearer, encouraging marginally detached customers and dapps to populate recent new lands.
Not So Quick
So, what issues stay? First, there’s the information availability drawback: what occurs when all the full nodes on a given sub-state disappear? If such a state of affairs occurs, the sub-state knowledge disappears eternally, and the blockchain will basically have to be forked from the final block the place all the sub-state knowledge truly is understood. It will result in double-spends, some damaged dapps from duplicate messages, and so forth. Therefore, we have to basically make certain that such a factor won’t ever occur. It is a 1-of-N belief mannequin; so long as one trustworthy node shops the information we’re high quality. Single-chain architectures even have this belief mannequin, however the concern will increase when the variety of nodes anticipated to retailer every bit of knowledge decreases – because it does right here by an element of 2048. The priority is mitigated by the existence of altruistic nodes together with blockchain explorers, however even that may develop into a difficulty if the community scales up a lot that no single knowledge heart will have the ability to retailer your complete state.
Second, there’s a fragility drawback: if any block anyplace within the system is mis-processed, then that would result in ripple results all through your complete system. A cross-substate message won’t be despatched, or may be re-sent; cash may be double-spent, and so forth. In fact, as soon as an issue is detected it could inevitably be detected, and it might be solved by reverting the entire chain from that time, nevertheless it’s completely unclear how typically such conditions will come up. One fragility answer is to have a separate model of ether in every substate, permitting ethers in numerous substates to drift towards one another, after which add message redundancy options to high-level languages, accepting that messages are going to be probabilistic; this may enable the variety of nodes verifying every header to shrink to one thing like 20, permitting much more scalability, although a lot of that may be absorbed by an elevated variety of cross-substate messages doing error-correction.
A 3rd situation is that the scalability is restricted; each transaction must be in a substate, and each substate must be in a header that each node retains observe of, so if the utmost processing energy of a node is N transactions, then the community can course of as much as N2 transactions. An method so as to add additional scalability is to make the hypercube construction hierarchical in some trend – think about the block headers within the header chain as being transactions, and picture the header chain itself being upgraded from a single-chain mannequin to the very same hypercube mannequin as described right here – that may give N3 scalability, and making use of it recursively would give one thing very very like tree chains, with exponential scalability – at the price of elevated complexity, and making transactions that go all the way in which throughout the state house way more inefficient.
Lastly, fixing the variety of substates at 4096 is suboptimal; ideally, the quantity would develop over time because the state grew. One choice is to maintain observe of the variety of transactions per substate, and as soon as the variety of transactions per substate exceeds the variety of substates we will merely add a dimension to the dice (ie. double the variety of substates). Extra superior approaches contain utilizing minimal cut algorithms such because the comparatively easy Karger’s algorithm to attempt to cut up every substate in half when a dimension is added. Nevertheless, such approaches are problematic, each as a result of they’re advanced and since they contain unexpectedly massively rising the fee and latency of dapps that find yourself by chance getting lower throughout the center.
Different Approaches
In fact, hypercubing the blockchain just isn’t the one method to creating the blockchain scale. One very promising various is to have an ecosystem of a number of blockchains, some application-specific and a few Ethereum-like generalized scripting environments, and have them “discuss to” one another in some trend – in follow, this usually means having all (or a minimum of some) of the blockchains preserve “gentle purchasers” of one another within their very own states. The problem there is determining how you can have all of those chains share consensus, significantly in a proof-of-stake context. Ideally, all the chains concerned in such a system would reinforce one another, however how would one do this when one cannot decide how worthwhile every coin is? If an attacker has 5% of all A-coins, 3% of all B-coins and 80% of all C-coins, how does A-coin know whether or not it is B-coin or C-coin that ought to have the better weight?
One method is to make use of what is basically Ripple consensus between chains – have every chain resolve, both initially on launch or over time by way of stakeholder consensus, how a lot it values the consensus enter of one another chain, after which enable transitivity results to make sure that every chain protects each different chain over time. Such a system works very nicely, because it’s open to innovation – anybody can create new chains at any level with arbitrarily guidelines, and all of the chains can nonetheless match collectively to bolster one another; fairly probably, sooner or later we might even see such an inter-chain mechanism current between most chains, and a few massive chains, maybe together with older ones like Bitcoin and architectures like a hypercube-based Ethereum 2.0, resting on their very own merely for historic causes. The concept right here is for a very decentralized design: everybody reinforces one another, fairly than merely hugging the strongest chain and hoping that that doesn’t fall prey to a black swan assault.









